Red wilds¶
Venturing into the red wilds means stepping into an environment that is part wilderness, part improvised cityscape, and entirely unpredictable. The terrain shifts between overgrown systems, creaking infrastructure, and the sort of engineered oddities only a committee meeting or a particularly creative guild could produce.
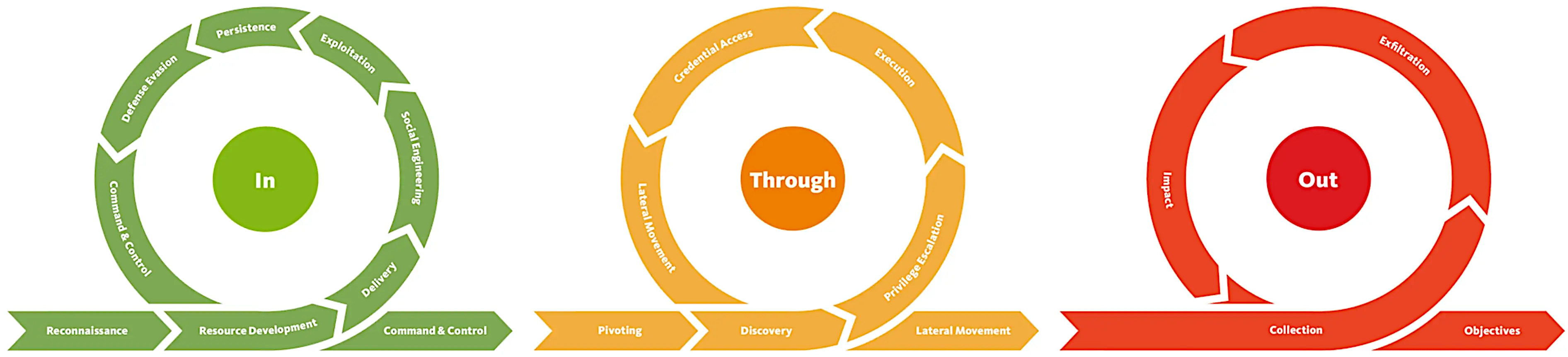
Here, methods and metaphors coexist with no intention of forming an orderly queue. One moment you find yourself in architecture worthy of a certain notoriously civic-minded city where nothing works as expected and yet, suspiciously, everything keeps running; the next you are tracing the clean, structured lines of a legacy kill chain through digital undergrowth.
Whatever, you watch your step.
Fox stealth. Raccoon grit. Squirrel-level entitlement.