Highway nut robbery: Blending in like a squirrel in traffic¶
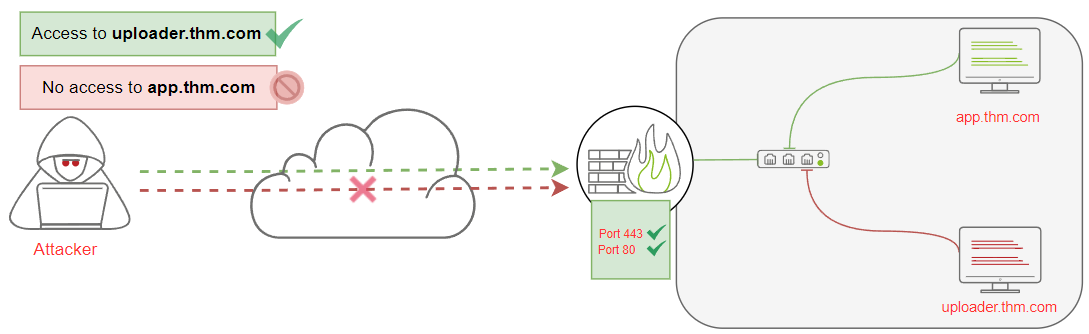
Practice data exfiltration techniques (in the THM Lab environment set up for it) to emulate normal network activities, such as DNS, HTTP, SSH, etc.
This content is from THM’s Data Exfiltration room, part of the Red Teaming learning path.
Why tunnel underground when you can waltz out with the loot in plain sight?