PE x86 0 protection¶
RootMe challenge: PE x86 - 0 protection: This challenge comes from greHack CTF 2012.
Retrieve the password to validate this challenge.
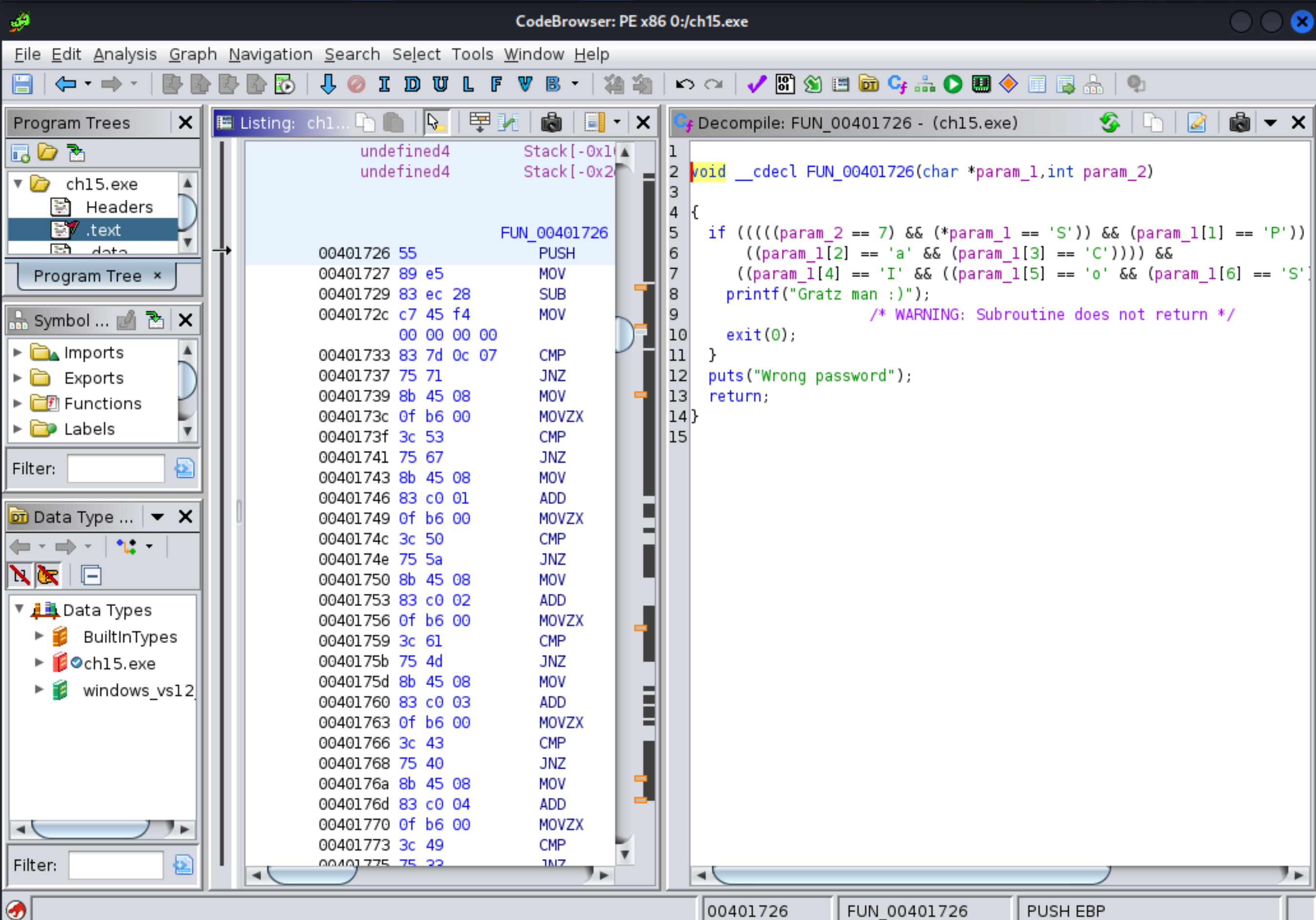
RootMe challenge: PE x86 - 0 protection: This challenge comes from greHack CTF 2012.
Retrieve the password to validate this challenge.
