DOM XSS in jQuery anchor href attribute sink using location.search source¶
Description¶
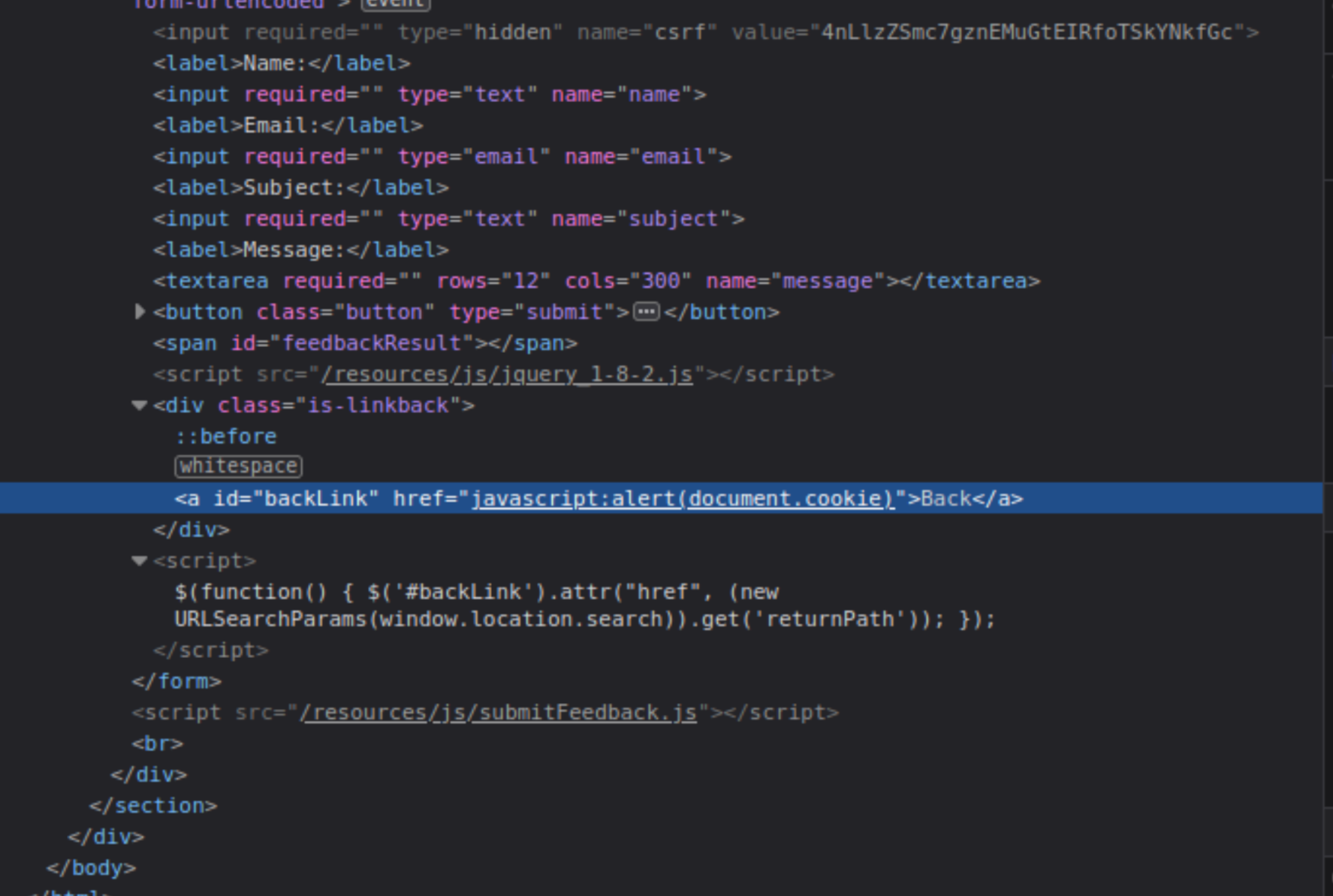
The website in this lab contains a DOM-based cross-site scripting vulnerability in the submit feedback page. It uses the jQuery library’s $ selector function to find an anchor element, and changes its href attribute using data from location.search.
Reproduction and proof of concept¶
On the Submit feedback page, change the query parameter returnPath to
/followed by a random alphanumeric string.Right-click and inspect the element, and observe that your random string has been placed inside an
a hrefattribute.Change returnPath to:
javascript:alert(document.cookie)
For example:
https://0a1800ac03209537c12be0bd005f00f0.web-security-academy.net/feedback?returnPath=javascript:alert(document.cookie)
Hit enter and click the
Backbutton on the site to trigger the attack.